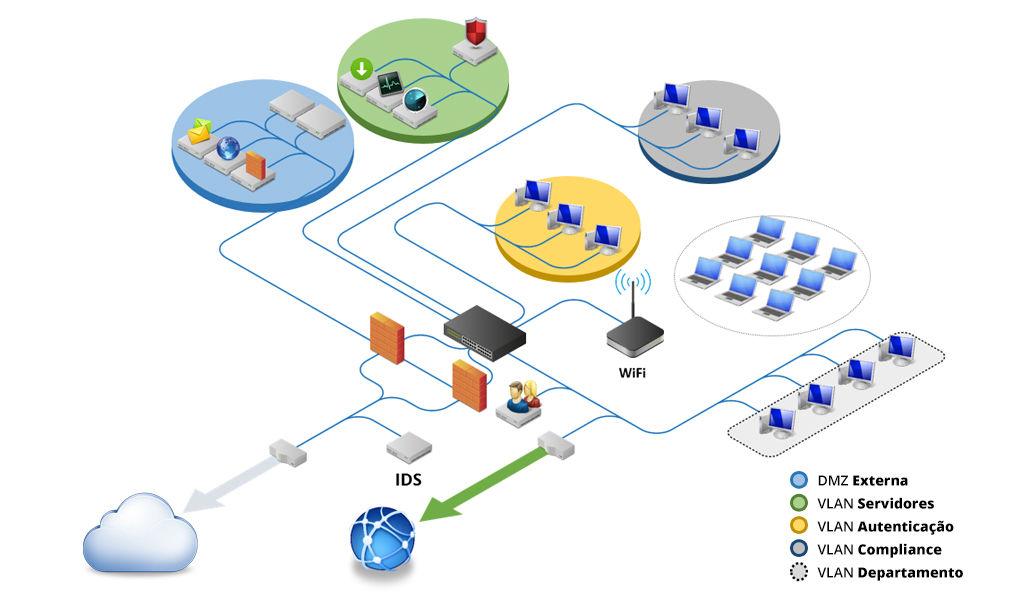
Network with high level of complexity due to the amount of internal assets, flows of people, traveling users and in accordance with the standards of information security. Often goes through auditing processes and receive access of new users, often outside the body of the company. If there are branch offices, seek ensure secure communication and high availability, as generally centralize their services in a single data center. Highly specialized team able to analyze, and correlate to screen all Project designed to identify vulnerabilities and implement securityNetwork environments with more than 500 users

Management and Firewall Monitoring

IDS / IPS
IDS/IPS

Anti-Spam Gateway
Gateway Antispam

Antivirus Management
Managed Antivirus

Network Access Control – NAC
NAC – Network Access Control

Web Application Firewall – WAF
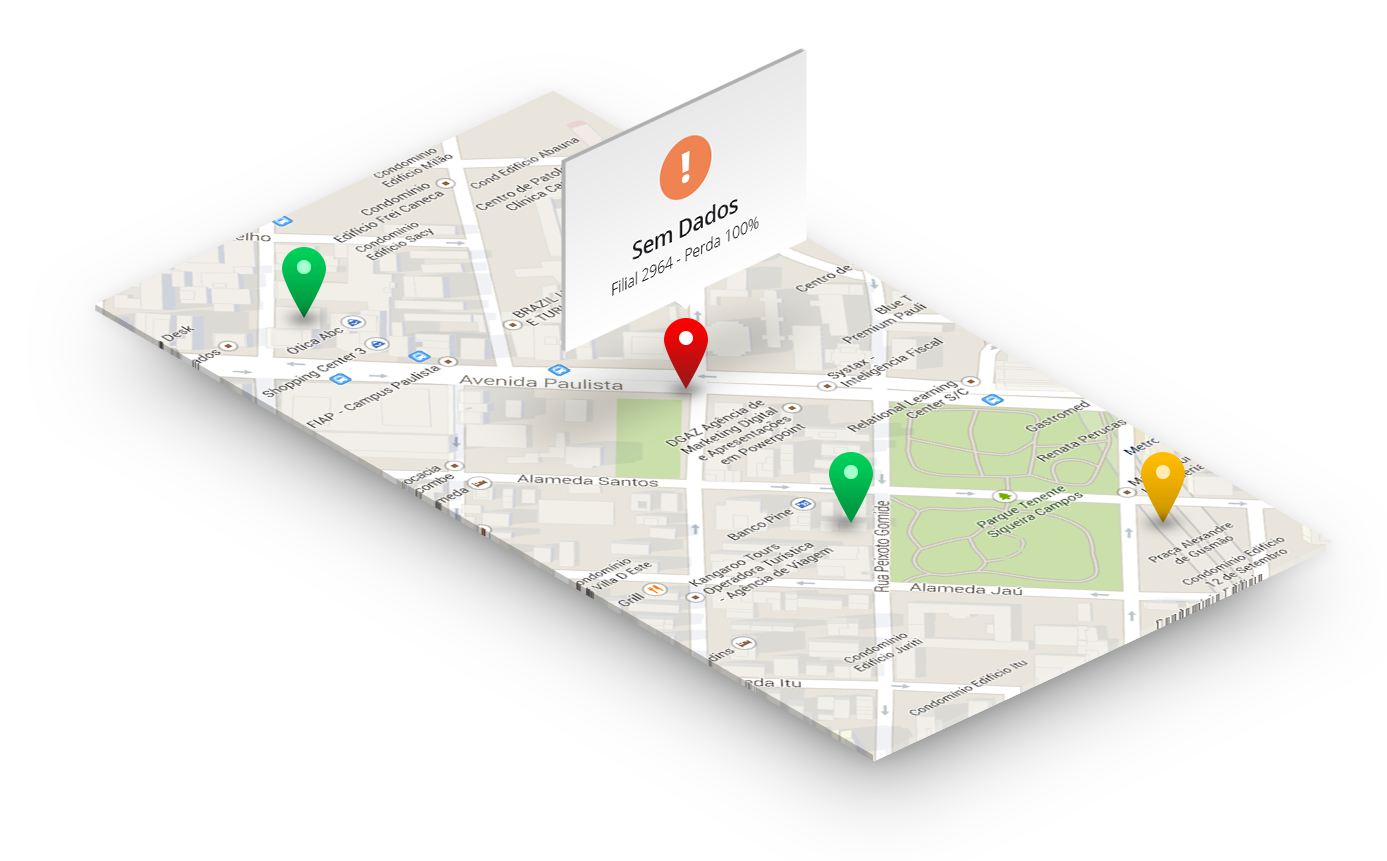
Assets, Links and Applications Monitoring
Links and Applications Monitoring
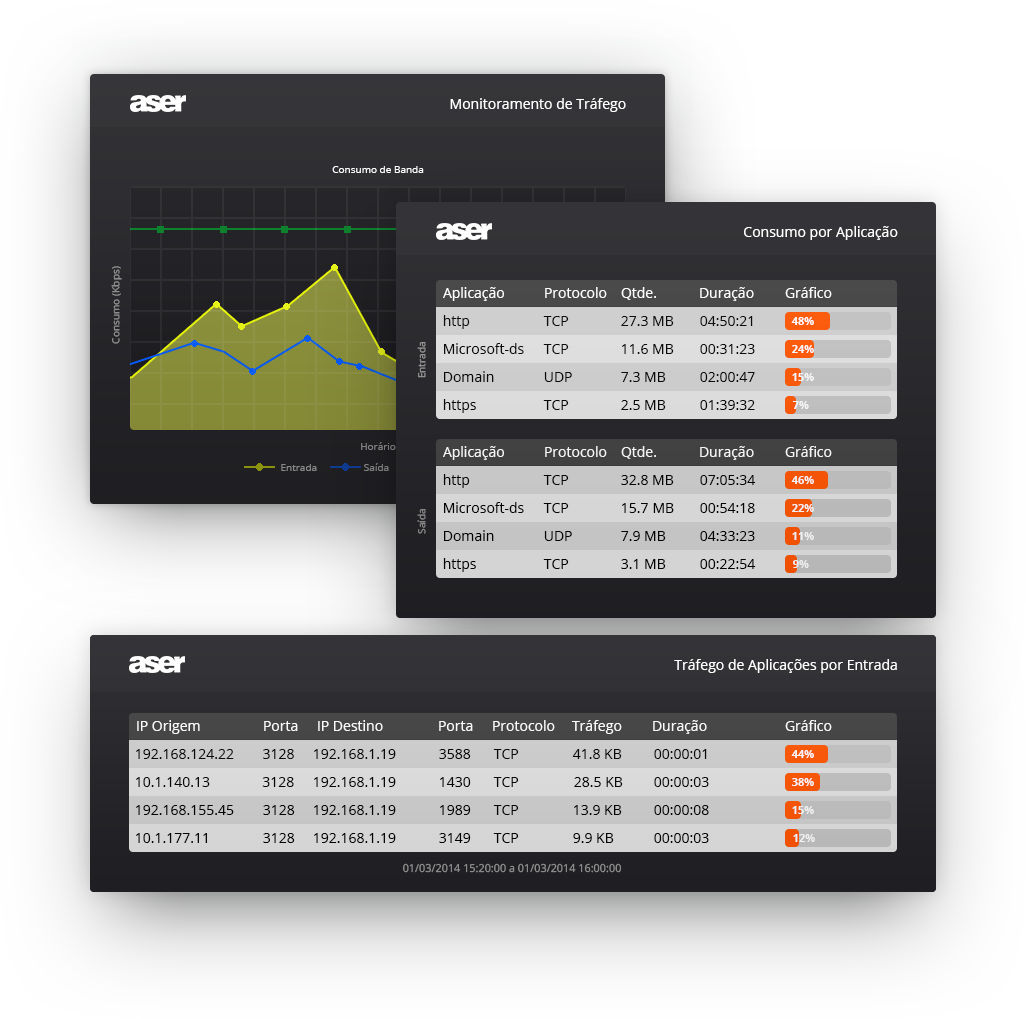
Traffic Monitoring
Traffic Monitoring (ITM)
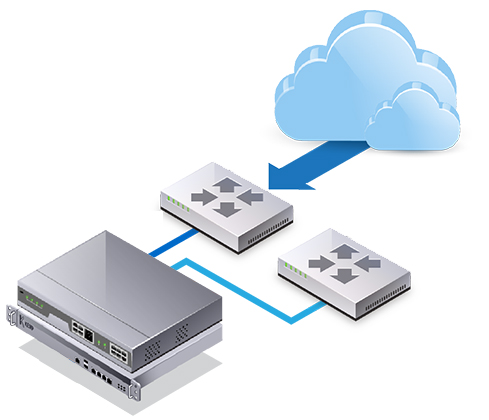
Link FailOver & Load Balance
Linkf FailOver & Load Balance

Incident Response Team
kinds of events, for the sake of your company and business. Working 24/7
reducing the response time, create proactive and preventive actions,
detail information and generate tools that enable better internal
management and minimize the negative impacts.
Insecurity Management
policies through:
Large-Sized Networks
CONTACT
Email: contato@aser.com.br
Phone: +55 (62) 3091-8010
ADDRESS
ASER Security – Goiânia
Street João de Abreu esq. with Street 9
N° 192 , Ala Terra – Rooms 61/63
Building Aton Business
West Sector / Goiânia – GO
CEP: 74.120-110
#24 Report Julho - 2022
#23 Report Junho - 2022
#22 Report Maio - 2022
#21 Report Abril - 2022
#17 Report Dezembro - 2021
#16 Report Novembro - 2021
#20 Report Março - 2022
#19 Report Fevereiro - 2022
#18 Report Janeiro - 2022
#15 Report Outubro - 2021
Report Agosto - 2021
Report Setembro - 2021
Report Julho - 2021
Report Junho - 2021
Report Maio - 2021
Report Abril - 2021
Report Março - 2021
Report Fevereiro - 2021
Report Janeiro
Report Dezembro
Report Novembro
Report Outubro
Report Setembro
Report Agosto