
Offensive Security
The Offensive Security service is used to help companies to identify potential vulnerabilities and / or existing and create remediation measures. Maintaining the security of your information and take preventive measures make impracticable industrial espionage and ensure that financial losses are minimized.
The Offensive Security service involves three main phases:



PHASE 1 | Fast Analysis
This phase aims to identify and validate the vulnerability exploitation opportunities resulting from poor or improper system configuration, known software failures, failures in the operational process and other causes too. In order to obtain the best results, Aser Security performs the “Fast Analysis” into 4 parts::
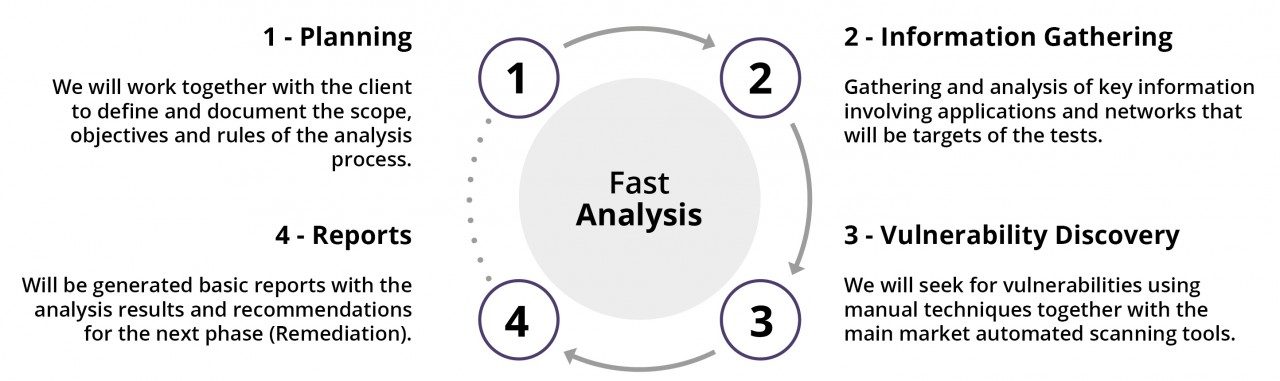
1: Planning
The experts of Aser Security, along with the client will work together to define and document the objectives of the tests, the scope and rules. We will conduct one or more interviews to better understand the goals and needs, security and compliance requirements, business risks and other related factors.
2: Information Gathering
The Aser Security team will collect and examine key information on specific targets and their infrastructure. This information is intended to assist the development of a test plan, and identify possible attack patterns in the chosen application or network, to provide appropriate guide the automated scanning software, and adjust more specifically the manual testing process.
3: Vulnerability Discovery
At this stage the Aser Security team will make use of expertise and automated tools to simulate attacks and find vulnerabilities.
For automated testing, our experts use tools to analyze web and mobile applications, or the target network, listing their resources and registering the most common problems. All vulnerabilities identified by the automated process are manually re-evaluated to ensure that they really exist and can be exploited.
During manual testing, our experts are collecting the information available to start their own attacks on applications or networks. The Aser Security team attempts to access real data and functionalities for fully demonstrate the significance of any identified deficiency.
4: Reports
Completing the process of intrusion testing, Aser Security offers to the client reports on the team’s findings. The reports include an executive summary for management and a list of priorities for development with practical recommendations for the correction of such vulnerabilities. Also will meet with the client’s technical team to discuss the test results and provide ongoing support throughout the process.
PHASE 2 | Risk Management
At this stage, the ASER SECURITY, along with you, will perform the risk evaluation and analysis of the results delivered to the PHASE 01 (Fast Analysis) and begin the remediation plan. At this time, we may have some risks highlighted in the tests that will raise some questions …
- What should be fixed first?
- How long can we keep the vulnerability without remediation?
- And if it is shown that the application of a particular supplier is presenting the biggest risk to the business?
- Should we recommend that our company no longer do business with this supplier of high risk?
The remediation process eliminates the root causes. When using legacy systems, which are not possible corrections of applications, the ASER side implements security mechanisms to mitigate the exploitation of these flaws.
At the end of the process, we will have a new security baseline defined in the environment.
PHASE 3 | SOC – Security Operation Center
Maintenance and continuous improvement. With the aggressive growth of persistent attacks, phishing and the cost associated with ‘recovery’ security strategies has advanced to the deployment of security operation centers, providing monitoring and continuous improvement of new vulnerabilities and attacks resulting from changes in the structure . The ASER SECURITY is prepared to provide a focused approach to incident response. We use a methodology that takes into account the organization’s support processes and existing standards in order to fit your way of doing business.
Are you interested or have any questions?
Request contact from one of our consultants!

